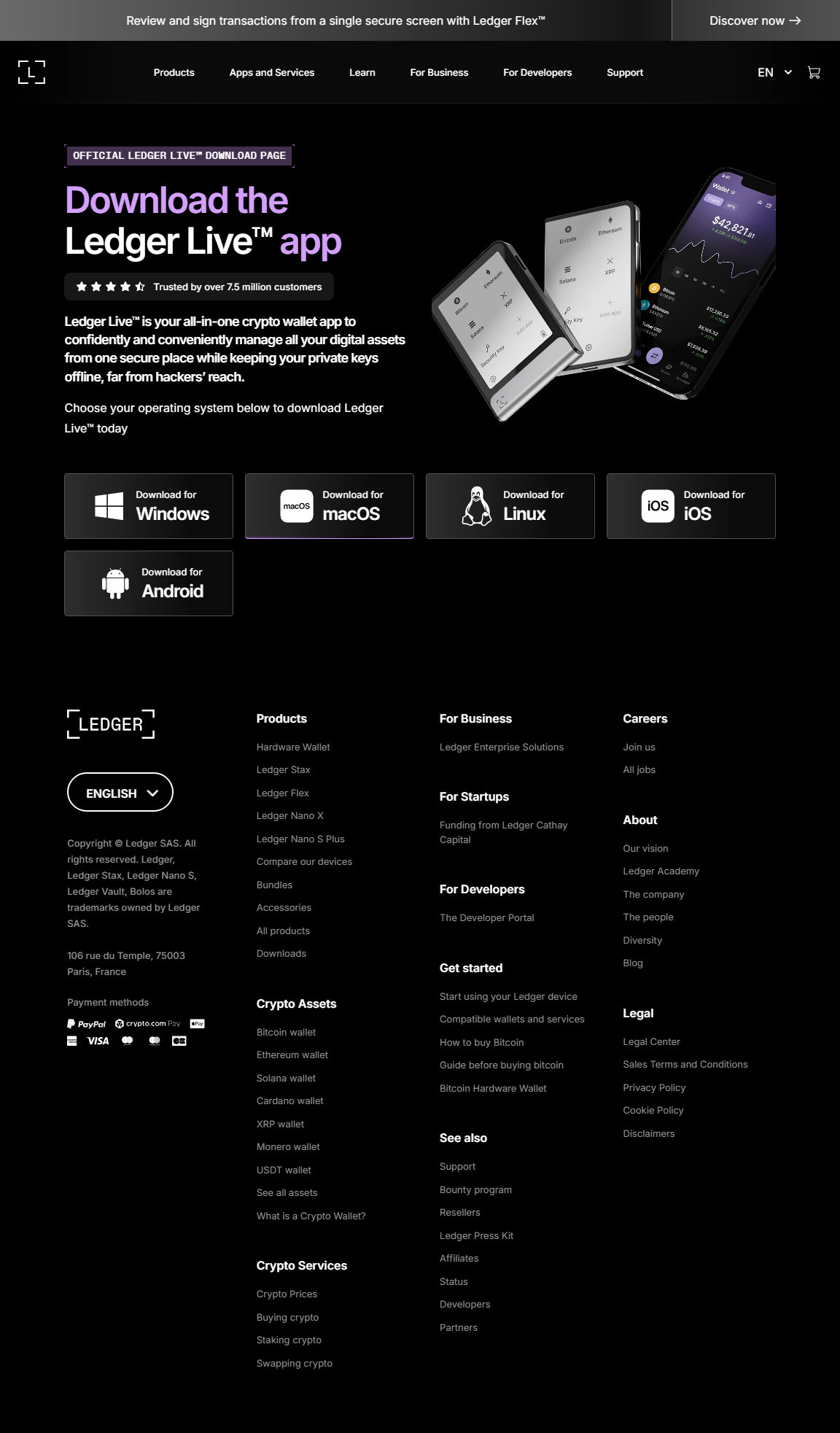
Ledger Login – Your Ultimate Guide to Safe Crypto Access
Discover how to securely log in to Ledger Live, connect your hardware wallet, and manage your digital assets like a pro without risking your private keys or security.
🔑 What is Ledger Login?
Ledger Login is the secure process of connecting your Ledger hardware wallet—such as the Ledger Nano X or Ledger Nano S Plus—to the official Ledger Live application. Instead of a typical username and password, Ledger login is based on cryptographic verification and physical device confirmation, ensuring maximum protection for your crypto portfolio.
This approach means that only you, the hardware wallet holder, can approve any access or transaction. It’s a revolutionary model of self-custody in the digital finance ecosystem.
🚀 Step-by-Step Guide to Ledger Login
Follow these simple yet crucial steps to safely log in and access your wallet via Ledger Live:
Step 1: Open Ledger Live
Download and launch the Ledger Live app from the official ledger.com website. Make sure your app is updated to the latest version to avoid compatibility issues.
Step 2: Connect Your Device
Plug in your Ledger device using the supplied USB cable (or connect via Bluetooth for Nano X). The app will detect your device and prompt you to unlock it.
Step 3: Enter Your PIN
Unlock your hardware wallet by entering your unique PIN directly on the device. This ensures no one can access your wallet remotely or through the app alone.
Step 4: Access Ledger Live Dashboard
Once authenticated, Ledger Live will open your portfolio dashboard. From here, you can view balances, send and receive crypto, or manage apps on your device.
🛡️ Why Ledger Login is the Most Secure Method
Ledger’s authentication process eliminates traditional vulnerabilities like password theft and phishing. Here’s why it’s a game changer for crypto security:
- Hardware-Based Verification: Access requires a physical Ledger device connected to your computer or phone.
- Offline Key Storage: Private keys are stored inside the device’s secure chip, never exposed online.
- Transaction Confirmation: Every operation must be manually confirmed on the hardware device screen.
- Phishing-Resistant: Without your device, no one can fake your login—even if they have your computer.
⚔️ Ledger Login vs Exchange Login
| Feature | Exchange Login | Ledger Login |
|---|---|---|
| Access Method | Email & password | Hardware device + PIN |
| Private Key Storage | Exchange servers | User’s hardware wallet |
| Security Level | Moderate | Very High (Offline) |
| Custody Type | Custodial | Non-Custodial |
| Phishing Resistance | Low | Extremely High |
⚙️ Common Ledger Login Issues & Fixes
- Device not detected: Try a different USB port or cable, restart Ledger Live, or reconnect the wallet.
- Firmware outdated: Update your device through the “Manager” section in Ledger Live.
- Bluetooth pairing failed: For Nano X, ensure Bluetooth is enabled and retry pairing.
- PIN forgotten: Reset your Ledger using your recovery phrase (24 words).
- Fake site alert: Only use the official Ledger Live app—never enter your recovery phrase online.
💬 Expert Tip
“Ledger Login transforms crypto security by removing passwords and placing control directly in the user’s hands. Every access is a cryptographic handshake between you and your wallet—no middlemen, no risk.”
❓ Frequently Asked Questions
1. Can I log in to Ledger Live without my device?
No. Your Ledger hardware wallet is essential for login authentication—it ensures your security.
2. Is there a web-based Ledger login?
Ledger Live operates as a desktop and mobile app only. Avoid websites claiming to offer Ledger login—they’re often phishing scams.
3. Can multiple people access one Ledger Live account?
Yes, if they share the same device and recovery phrase—but this is strongly discouraged for security reasons.
4. How often should I update Ledger Live?
Always keep Ledger Live and your device firmware up to date to ensure compatibility and protection from emerging threats.
🔒 Final Thoughts on Ledger Login
The Ledger Login process is the foundation of true crypto security. By combining offline authentication, physical confirmation, and encrypted access, Ledger gives you complete control of your digital wealth. In a landscape where privacy is power, Ledger ensures your coins stay exactly where they belong—with you.